Microsoft has a tool called pktmon that give you a stripped-down version of NPCAP that can be used to get Packet Captures from Windows machines without having to install a third-party piece of software. It’s not horrible to configure from the command line and you can go that route if you wish but for most use cases and end users just getting into Packet Log Investigation its can be a pain. I don’t think you’ll need any help, as if you are already looking to get a deeper understanding of your client network traffic and this helps you get there. Worse case if it doesn’t work for you can always do it the standard supported way. I have included the source script and have converted it to an executable to make it easier to run for those that don’t have much Powershell experience. The way you launch it is just double click the .exe, it loads PowerShell in the background and launches a GUI that looks like this. It will automatically create the C:\PacketCaptures location and since this is my script I am not changing it. It makes it easier for me to find the files after its complete. The warning below is just telling you that it needs to be run with Administrative permissions so that pktmon can interrogate your network interfaces.
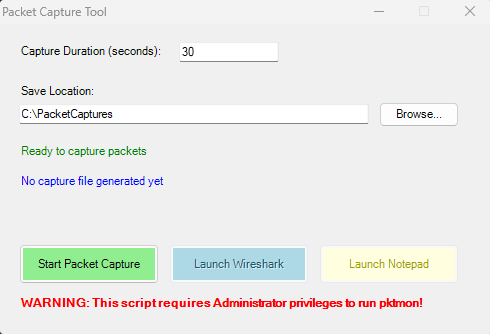
When you launch it by right clicking and then clicking run as administrator it will look like this.
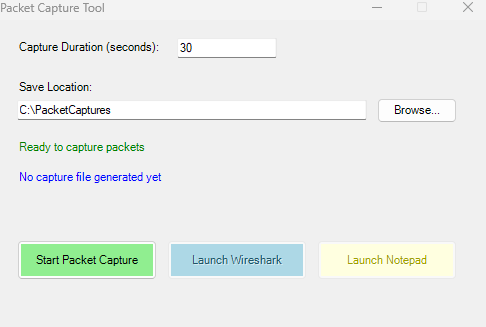
By Default the Capture Duration is 30 seconds. You can adjust it up or down, whatever your needs are. Its good to start the capture if possible and then work in the application you are having issues with for a set amount of time.
Once the timer completes it will generate two files by converting the ETL file into a PCAP and a TXT file. The reason I am doing both is because AI is your friend and it can parse the TXT file to give you some insights into what to look at. The PCAP can be parsed by WireShark if needed.
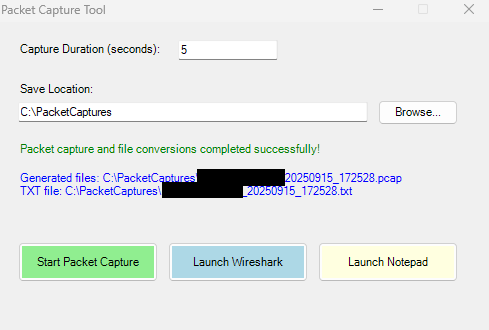
In the example below I ran it on my test machine for 5 seconds and it outputted two files and lit up Launch WireShark and Launch Notepad. All computers have Notepad by default, WireShark would need to be running on the machine for that button to work. If you have WireShark on another computer, you can copy the PCAP to it and do your tracing there. It also includes a time date stamp on the file so you can run it over and over to get .PCAP and .TXT files over time.
Included in the PacketCapture.zip is the Powershell Script that I based the .EXE off of, you can run it either way, just make sure that you run with Administrator permissions. Like all scripts your responsible for its use and while it works well for me, your mileage may vary.
